L2Connect Usage Models
L2 Connect to achieve secure network environment
With the emergence of SoftEther, which achieves virtual private network (VPN) at a layer 2 level with low dependencies on applications, building a virtual private network (VPN) at a layer 2 level has come to be known by general public as well.
The biggest advantage of virtualizing at Ethernet (layer 2) level is to build a system independent of all the transport protocols or applications transmitted through the network, enabling virtualization of the network (VPN) without changing the applications you operate at present.
We realized the advantage, proposing solutions to users as well as developing and selling L2 VPN software. Bizmobile takes the needs of corporate users and developed L2Connect that provides excellent performance capable of supporting enterprise-level, large-scale businesses, as well as the management capabilities of many clients.
Achievement of overlay network
What L2Connect proposes is to build a virtual private network (VPN) at a layer 2 level spanning multiple different networks with a simple installation and management method. This is the technology called “Overlay network” that builds a virtual network (VPN) on an existing physical network.
Various overlay network can be considered. For example, you can build a virtual network, not only within your company, but also extending across associated companies, outsourcing contractors, clients, etc. over the internet, and then, use common applications within the network. Or, when servers are down, you can prevent the suspension of your business by connecting to the mirrored servers at another site automatically with a virtual network. You can build a virtual network that does not depend on the existing network, permanently or temporarily, and operate your network flexibly. In addition, the license of flexible pricing structure is available for BCP measures.
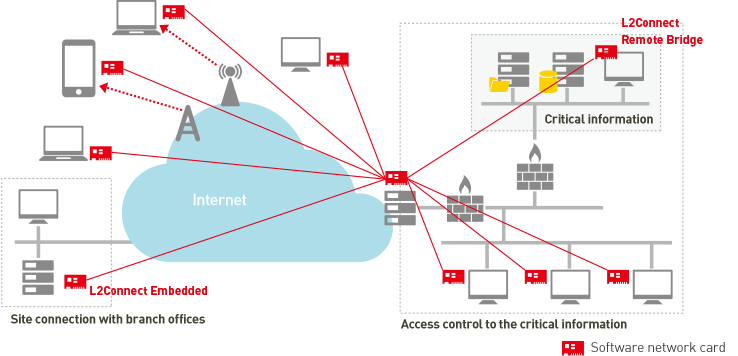
L2Connect is treated as a general VPN product, but it is a solution capable of building overlay network so as to be used for wider purposes.
Why L2Connect is needed
The unique characteristic of L2Connect is that even though it is a technology virtualizing at a layer 2 level, it does not introduce Client/Server system.
The other technologies such as SoftEther (PacketiX) install a virtual NIC which acts the same as Ethernet NIC to client in order to emulate Ethernet. Those are the typical client/server solution, achieving virtual private network (VPN) by setting up a separate virtual hub and connecting to it (like connecting virtual twist-pair cable).
Virtual Ethernet requires to create a routing table and to control a packet flow to a certain extent, and it is completely recognized as NIC from applications, therefore, no changes to the existing applications are needed.
Similarly, the virtual network of L2Connect is seen only as ordinary Ethernet from applications, but L2Connect itself act like a switch, not emulating Ethernet NIC or hub.
All computers which compose L2Connect network act as virtual switch the same way, and if you establish connection between each virtual switch like connecting cables, the virtual switch see each MAC address and can deliver packets to each destination virtual switch. That is, L2Connect does not have a concept such as client or server, and all composing member are treated equally. (Other than L2Connect, Open VPN, which is an open source, takes a similar form).
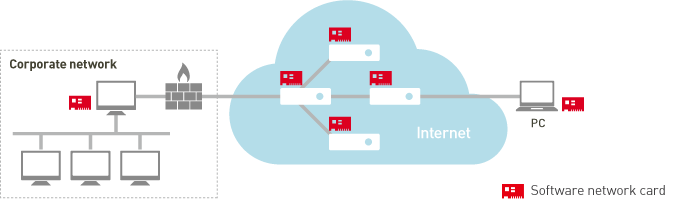
Therefore, when building a large-scale virtual network, you do not need to control traffic by the maintenance of routing table, and can operate by establishing a connection just like switching a cable as necessary. This ease of operation is one of the advantages of L2Connect.
In addition, by introducing the system emulating switch, not Ethernet NIC, the architecture has become simple and it has become easier to improve performance. The characteristic that the decentralization of traffic is easy is a key point in terms of improving performance, too.
Easy to connect, Easy to introduce
It is quite easy to build a virtual network using L2Connect. IPsec is another method to build a virtual network that does not depend on applications. But IPSec is a virtualization of layer 3, i.e. virtualization of IP; and there was a problem that you often needed to execute some configurations on a gateway in order to pass through the gateway such as firewall or NAT.
On the contrary, L2Connect achieving layer 2 on the IP network via SSL enables a transparent communication from anywhere and with any applications, without such particular configurations.
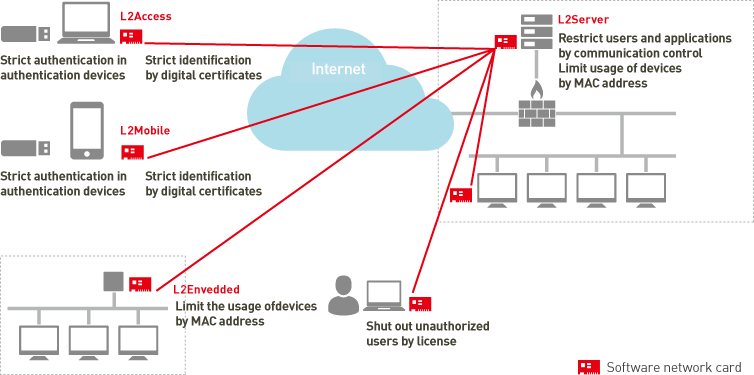
Furthermore, L2Connect has a license for embedded devices as well, and actually small-size adapter in which L2Connect is embedded is sold. By using this, telecommuters and small-sized branch offices can join the network easily with maintenance-free.
<OA Telecom Service Corporation case - VPN system Thin client for “L2Connect”>

Supporting SNMP in the aspect of management as well, it is easy to embed a virtual switch into the management system of entire network. By using the attached switch manager, you can perform centralized management without separate management tool.
The product also has the advantage with regard to the distribution / placement of client software to user PCs. In addition to general installation by setup.exe, you can choose methods including: distribution by optical disk using the auto run feature; installing from Web site using ActiveX; and, automatic installation by inserting USB memory. Of course, silent installation is supported, so if an administrator configures appropriately, no particular installation work is necessary at user side.
A high quality of security and usability
There is a security side of functionality as well. In addition to supporting RADIUS authentication by general ID and password, it also supports the authentication by digital certificate. You can also utilize external authentication devices such as USB key.
Furthermore, in SoftEther, as client software is recognized as NIC on Windows, it is possible to bridge to the intranet easily by the function of Windows itself. On the other hand, L2Connect protects unintended connections by separating licenses; one is the client for ordinary access (L2Connect Remote Access) and another is the client that is capable of bridging (L2Connect Remote Bridge).
In addition, L2Connect can distinguish which client software is used by a receiver, so you can limit the users or devices capable of bridging, and avoids the generation of security holes by the operations at client-PC side. Needless to say, access control by MAC address is possible.
With regard to encryption as well, L2Connect uses OpenSSL, and therefore, has an advantage of updating promptly just in case a vulnerability is found. As OpenSSL is open source used widely, it is also important that its security level or the strength of encryptions, bugs, etc., have been proved.
L2Connect has considerable track record of large-scale operations, demonstrating high scalability even in the scale of several thousands of virtual networks. As we have been involved in a layer 2 virtual network solution from its foundation, we have lots of past cases as well as a considerable track record of support. Feeding back those results, we designed to establish overlay network as simple as possible while keeping a high level of security.
Acting in concert with mobility, functionality, and safety of L2Connect, it is possible to combine with third-party products which works with L2Connect.
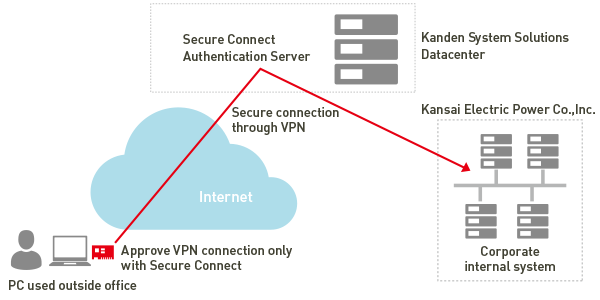
<Kanden System Solutions Co., Inc. SECURE CONNECT case>
Best for telecommuting (teleworking)
The most comprehensible way of letting workers use their private PCs for business is to remotely control office PCs from their home.
As the office PCs are remote-controlled, you do not need to purchase additional licenses or applications of virtual PC, or to migrate data to a cloud service side. PC environment remains unchanged, and enables “working with the PC of the office in the morning and working with the private PC at home from the afternoon”.
Windows standard function, “Remote Desktop” is utilized for building this system.
Two systems are needed to realize this system. One of which allows you to login to in-house LAN via the Internet using VPN, and another of which turns on PCs of the company remotely.
In the system that allows you to login to in-house LAN via VPN, devices are configured so as to utilize the communication protocol (RDP) of Remote Desktop. In the system that turns on PCs remotely, motherboards loading Intel’s “vPro Technology” or LAN cards with “Wake On LAN” function are used.
<KDDI Corporation Telecommuting system case>
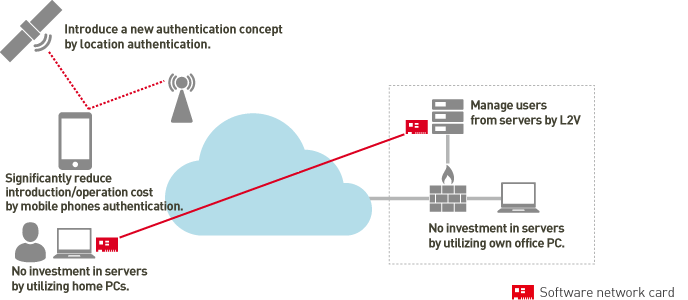
KDDI has worked toward adopting a telecommuting system to secure a work-life balance for their employees. This unique system uses “L2Connect”, and it is highly regarded to go so far as to win the Telework Excellence Award. The system supported BCP immediately after the earthquake disaster of 3/11, and played an active part in subsequent power saving measures.
Step-by-step introduction is possible
In addition to its simple configuration and operation, software alone achieved excellent flexibility and security. As there is no need to re-configure existing network devices, you can start from small-sized trial and expand to larger network confirmation and don’t need to re-establish systems or applications at a time.